Since RYUK’s inception back in August of 2018, its operators have earned an estimated $150 million worth of Bitcoin worldwide. That is a lot of money in a short period! I’ve had the opportunity to work with RYUK ransomware a few times, and my mom’s nursing facility was a victim, so I thought I would cover the topic in today’s article. I will also discuss some tips on better preparing against ransomware.

UHS Security Incident
At the pinnacle of the Covid-19 pandemic late last year, Fortune 500 hospital and healthcare services provider Universal Health Services (UHS) was hit by the Ryuk Ransomware Attack. UHS has over 90,000 employees servicing roughly 3.5 million patients across a network of more than 400 healthcare facilities in the US and the UK.
The ransomware attack was a significant incident and naturally forced UHS employees to shut down all IT applications and systems to prevent the malware from spreading throughout the rest of the network. This, of course, made a grave impact on the day-to-day operations for serving their 3.5 million patients with their computer systems and online patient records being unavailable.
My mother, who is a nurse at a UHS facility in Corona, witnessed this destruction firsthand. Hospital facilities during this pandemic are already chaotic as it stands but having no access to the online charting systems was a nightmare, and they had to do all the nurse charting on paper. Fortunately, they were able to restore systems back to normal with third-party security vendors and forensic analysts.
What is RYUK Ransomware?
Based on information shared with Bleeping Computer by Advanced Intel’s Vitali Kremez, the attack on UHS’s system likely started via a phishing attack,” BleepingComputer says.
The initial foothold will typically come from phishing emails and the use of Emotet. Emotet is a trojan that is primarily spread through spam emails. The infection may arrive either malicious script, macro-enabled document files such as excel and pdf. It only takes one unsuspecting user to click on the link to allow the attacker into the environment.
Once the initial system is compromised, the attackers will use several techniques to push out the Ryuk binary through-out the target victim’s environment. Crowdstrike has compiled a list of some commonly observed network events which include:
- A PowerShell script is executed and connects to a remote IP address.
- A reverse shell is downloaded and executed on the compromised host.
- PowerShell anti-logging scripts are executed on the host.
- Service User Accounts are created.
- Privilege escalation techniques continue until credentials are obtained to access a domain controller.
Group policy objects are used to push out the Ryuk binary to all hosts within the domain.
RYUK Footprints
Once the Ryuk binary has been injected onto a host, it will encrypt all non-system files on the system. It will not encrypt files with the extensions dll and exe. Remember, the computer needs to remain operable for the victims to see what precious files they’ve lost access to.
All the encrypted files will have their extensions changed to .ryk. Also, a ransom note labeled as RyukReadMe.txt will be in the folder with the encrypted files.
In previous builds of Ryuk, the attacker’s Bitcoin address would be included in the message. However, in current builds, they’ve removed the address and only includes their email for methods of communication, as shown below:

How to Prepare Against RYUK Ransomware
Here are some of the top best practices you can consider when preventing and preparing ransomware attacks:
Phishing Awareness
This is probably the most important tip on this list. You know the saying that humans are the weakest link. It is very much real, and attackers know this, so most successful ransomware attacks have the root cause of phishing.
It’s recommended that all employees within an organization participate in regular phishing training to be aware of the dangers and consequences.
Implementing a sound EDR system
Endpoint detection response (EDR) systems are vital in combating ransomware attacks and malicious activity in general.
CrowdStrike is a great EDR that many organizations use today to detect and prevent incidents such as RYUK ransomware. It works by installing agents on each endpoint in your environment. Anytime CrowdStrike’s machine learning algorithm detects a hit, CrowdStrike will automatically flag and alert and many times quarantine the suspicious action or file.
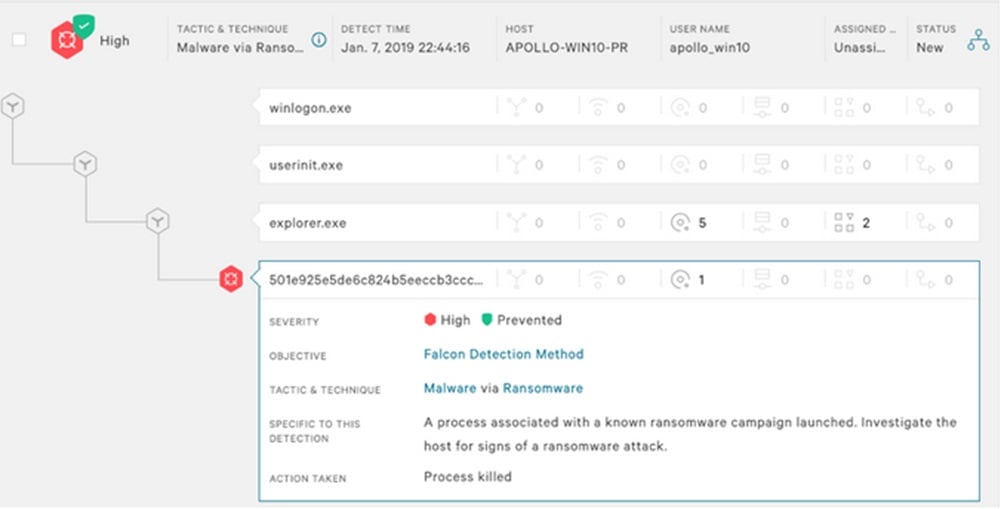
Well-protected Backups
Having reliable backups will remove most of the threat of a ransomware attack altogether. What’s the worry of encrypted files when you can just restore them from your back-ups?
The importance here is, having a reliable backup system in a location separate from your network environment. If your backups are located in the same network, then RYUK will either encrypt or erase the backups on your network.
A great example is Rubrik’s ransomware-immune backups. Rubrik’s file system is built to be immutable, meaning backups cannot be encrypted or deleted by ransomware.
A great demo on how this works can be found here: https://www.rubrik.com/en/solutions/ransomware-recovery
Conclusion
That pretty much wraps up this blog post. I truly hope you found this article useful and learned a thing or two about ransomware and how to prepare against it. If you have any questions about any of the article’s content, please feel free to reach out to me at bryan.macario@tec-refresh.com; I’d be happy to answer them! Thanks for reading, and stay tuned for more content!
References:
- Ransomware Recovery – https://www.rubrik.com/en/solutions/ransomware-recovery
- Big Game Hunting with Ryuk: Another Lucrative Targeted Ransomware – https://www.crowdstrike.com/blog/big-game-hunting-with-ryuk-another-lucrative-targeted-ransomware/
- UHS restores hospital systems after Ryuk ransomware attack – https://www.bleepingcomputer.com/news/security/uhs-restores-hospital-systems-after-ryuk-ransomware-attack/
As a Managed Service Provider (MSP) and Managed Security Services Provider (MSSP), we manage your IT services, offer backup and disaster recovery, and provide network visibility and security. Our knowledgeable and customer-oriented staff engages to accelerate your network and simplify its security, visibility and automation. Questions? Contact Tec-Refresh, Inc.
