Have you ever opened up a web browser and typed in the URL: https://www.goggle.com by accident?
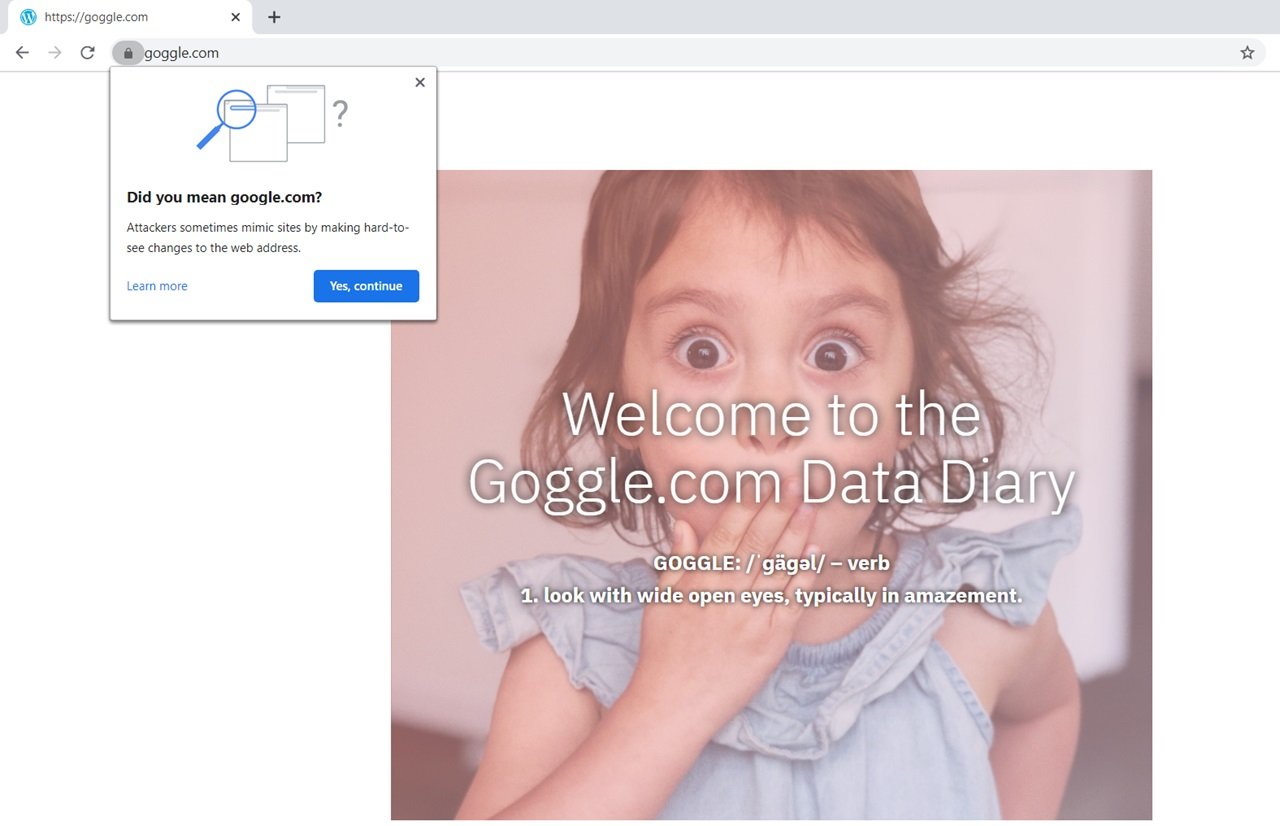
If you did, then you might have immediately realized that you typed “google” incorrectly. You may notice that the content is off, or if you’re using Chrome, then Google will suggest that you visit www.google.com.
Major companies try to anticipate typographical errors and purchase misspelled versions of their domain so that users will get redirected to the site that they intended to visit. Google was able to acquire the domain www.gogle.com such that if you were to miss the “o” in their URL, you would be directed to Google’s website. However, this is an ideal situation, and it does not always happen, as evidenced by our first example.
You can probably imagine how this common human error can be anticipated and leveraged by attackers.
Typosquatting is a social engineering attack that relies on a victim to confuse the domain they intended to visit with a malicious one.
Typosquatting, in all its different variations, intends to benefit the attacker at the cost of the victim. This trap leverages a victim’s trusting relationship with a particular organization, and it can download malicious code or coerce a user to provide sensitive information. Imagine if an attacker could register the fully qualified domain www.bankofamerca.com with a domain registrar in combination with being issued a web certificate from a certificate authority. When the web page loads, the user would notice a lock icon in the URL bar indicating that the connection with the host is secure and that they are who they say they are. At this point, all an attacker would need to do is fashion their website to look and behave like Bank of America’s website. When the user puts in their credentials on to the webpage and presses enter, the web page would then send the data to the attacker’s database. The user would receive an error indicating that the credentials did not match the records in the database. Due to lacking awareness about this form of attack, the victim may never assume they gave away one of their most valuable assets.
Social engineering attacks bring to light the need for organizations and individuals to practice good security hygiene. Reusing a password across multiple accounts can be an issue even if, by some miracle, you do not suffer from the human condition and make typographical errors. Data breaches are all too common in today’s world. You might have heard that Myspace, Sony, Zynga, etc., have all had their data breached. Hackers may sell user information such as user credentials for money, and sometimes that information is published on the internet.
Tip: Check out https://haveibeenpwned.com/ to see if any of your accounts have been breached.
One way to mitigate the risks associated with someone getting a hold of your credentials is to use a strong and unique password for each account.
Avast published an article in 2019 illustrating the scale of the issue as “83% of Americans do not include all of the following when creating passwords: numbers, special characters, upper and lower case letters, and do not create passwords that are at least ten characters long.”1 The same article mentions that 53% of Americans also use the same password across multiple accounts.
It is impractical for most people to remember a random string of lowercase and uppercase letters, numbers, and symbols 20 characters in length for just a single account. A password manager is a viable solution in this case as it does an exceptional job of blending together elements of security, practicality, and functionality. With a password manager, you are required to generate a single strong password for your account. When you decide to change the password for your accounts, a password manager like LastPass will help you randomly generate a strong password to use. It will then prompt you to save the username and password such that when you visit the website next time, your credentials will be automatically filled in. Your password manager account must be configured with multifactor authentication (MFA) in order to ensure that a hacker is not able to access all your information with a single password.
Microsoft claims that 99.9% of attacks can be blocked by enabling MFA.2 An account adequately set up with MFA can deter a hacker that has access to your username and password. As the name would suggest, this is because you are required to provide a token along with your username and password to authenticate into your account. The most common medium of receiving a token is either through your email or your phone. Each time you log into your account, you are required to provide a unique one time use short-lived token to authenticate into your account. This would mean that a hacker has no plausible means of accessing your account unless they have access to your phone or email address.
Common attacks like typosquatting highlight the need for every single individual in a business or personal setting to practice good security hygiene. Following acceptable security practices is not an unrealistic platonic ideal; it is actionable, feasible, and functional. In this case, the only prerequisite for peace of mind is some time out of your day.
Sources:
- https://press.avast.com/83-of-americans-are-using-weak-passwords
- https://www.microsoft.com/security/blog/2019/08/20/one-simple-action-you-can-take-to-prevent-99-9-percent-of-account-attacks/
As a Managed Service Provider (MSP) and Managed Security Services Provider (MSSP), we manage your IT services, offer backup and disaster recovery, and provide network visibility and security. Our knowledgeable and customer-oriented staff engages to accelerate your network and simplify its security, visibility and automation. Questions? Contact Tec-Refresh, Inc.
