In today’s article, I will discuss an open-source tool that complements Windows Event Logs, called Sysmon.
This tool is part of the Windows Sysinternals Suite and was developed by Mark Russinovich. The whole idea of Sysmon Is that it further increases the logging capabilities that Windows Event Logs were designed to do. Sysmon is an excellent tool for incident response, threat hunting, and generally having better visibility on what’s going on in the environment.
Installing Sysmon:
- This link provides step-by-step instructions on installing Sysmon via the command line.
- https://github.com/trustedsec/SysmonCommunityGuide/tree/master
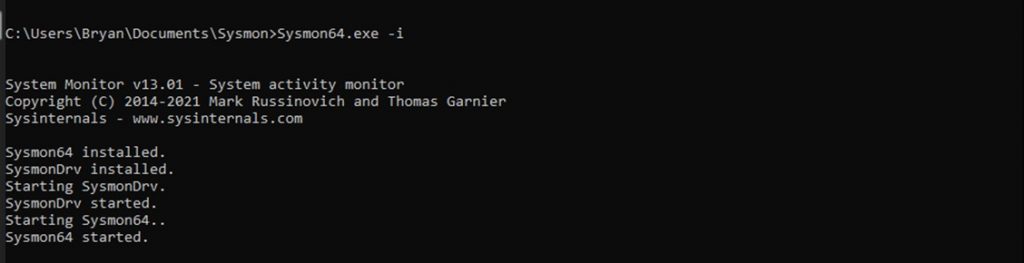
- Sysmon.exe is easy to deploy on any Windows Device. The current version allows the following command to install the default driver and start the Symon service:
“Sysmon64.exe -I.”
In most cases, you will also need to include the Sysmon XML configuration file. The configuration file aims to provide filtering, enabling certain functions and preventing too much noise from coming in. A great one to use is Swiftonsecurity’s sysmonconfig-export.xml from https://github.com/SwiftOnSecurity/sysmon-config.
To locate the Sysmon logs:
Open Event Viewer > Applications and Services Logs > Microsoft > Windows > Sysmon > Double-click on “Operational”
The source will say “Sysmon,” and the Event IDs are unique to the Sysmon tool. As shown below:
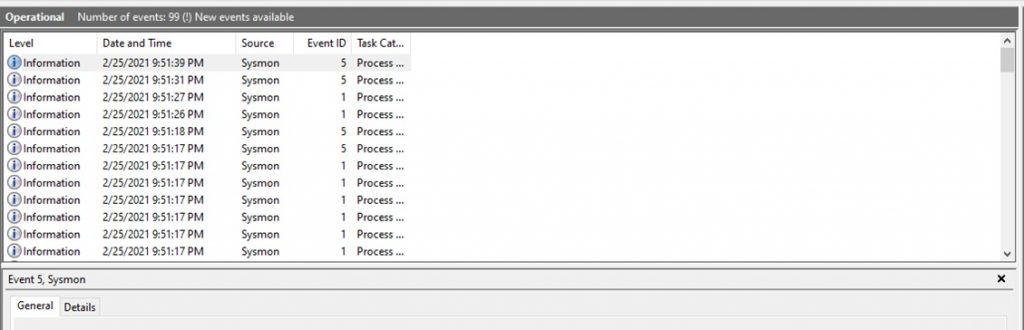
As you can see, the Event IDs are not the same numbering convention as Windows Event Viewer. Now I am going to explain the most common Sysmon Event IDs used for threat detection.
Process Creation (Event ID 1)
This Event ID shows the log entry for any processes that started on the host device. This is great for figuring out if there were any malicious programs ran on the host device. It will even tell you what the parent image process was. The parent image process is essentially the parent process that executed the process creation.
Network Connection (Event ID 3)
The Network Connection logs are disabled by default, but they log all the TCP/UDP connections to the machine when enabled. It will also include the source and destination hostnames, IP addresses, and port numbers. This is one of the most useful Sysmon logs because you can traceback any potential C2 connections to your host device.
Registry Actions (Event ID 12,13,14)
Sysmon provides 3 primary registry logs:
- Event ID 12 (Registry Object added/deleted)
- Event ID 13 (Registry Value set)
- Event ID 14 (Registry Object renamed)
This ensures that any potential malicious changes done to the Windows Registry do not go unnoticed.
File Create Time Change (Event ID 2)
This log attempts to detect techniques that modify the timestamps of a file. Attackers may do this to prevent detection by hiding dropped files or accessed files.
Registry AutoRun (attack scenario)
Jymcheong’s Sysmon Resources provides a great collection of Sample Data that contains actual malicious observations. I wanted to go ahead and cover one in particular, which is the Registry Autorun.
In this example, Jymcheong runs an Empire PowerShell command to abuse the HKCU registry setting to run an EXE.
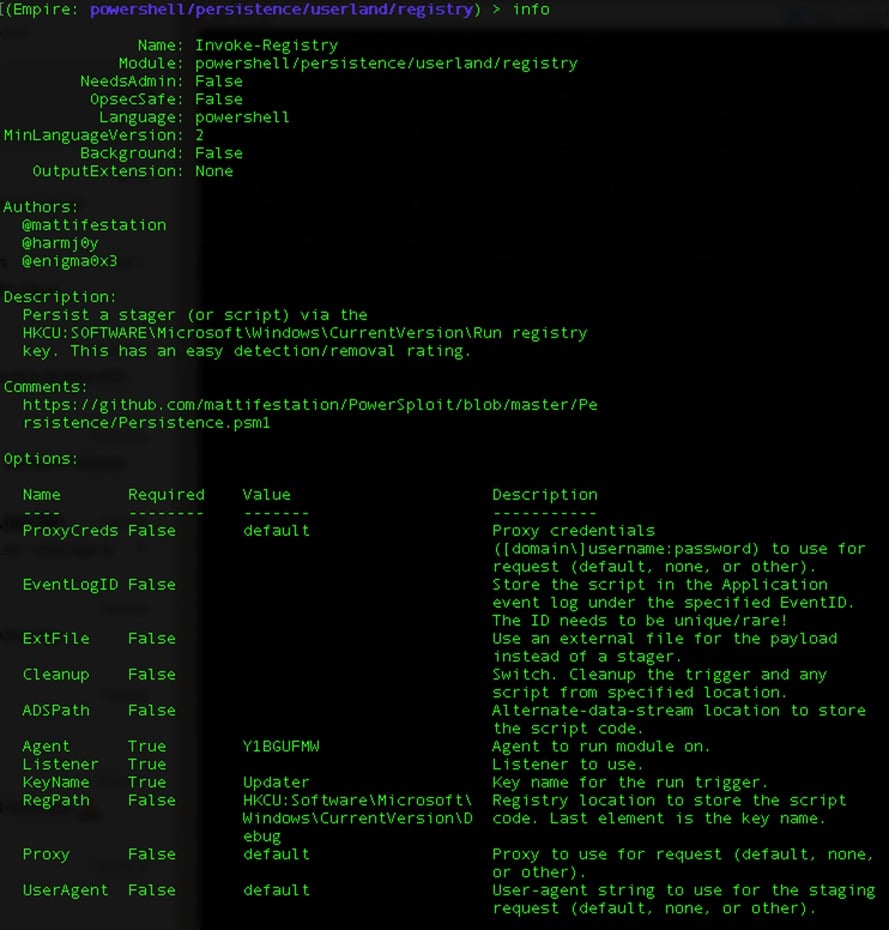
Empire is typically used as a post-exploitation Windows tool. It’s used to gain further access after the initial foothold access has been obtained.
As a result of the Empire “Run registry” command, the following Sysmon Event Logs has been generated:
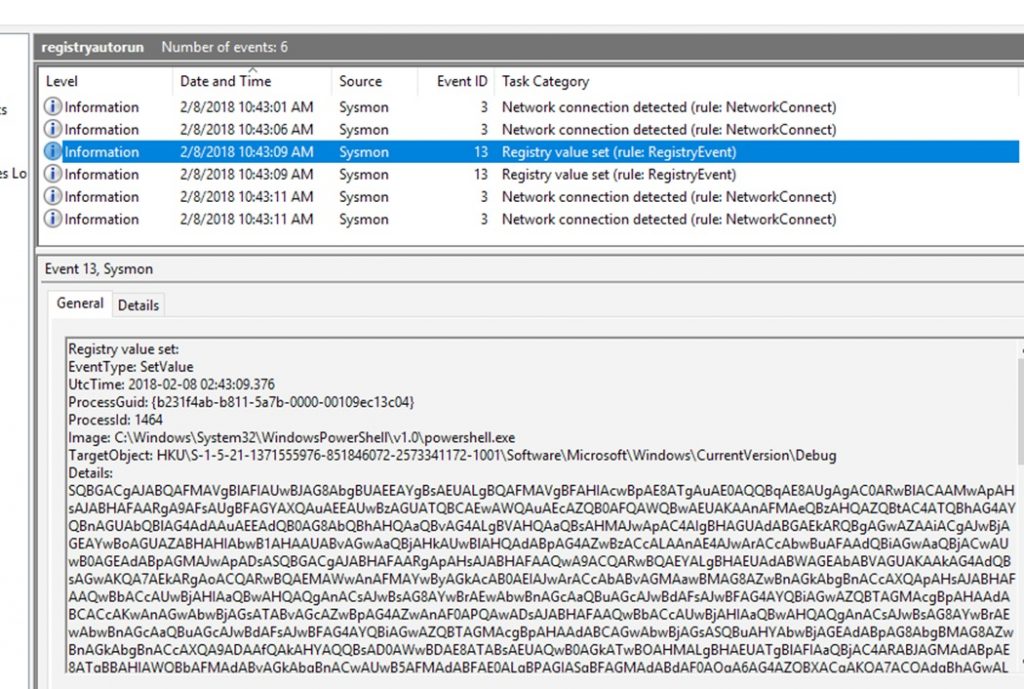
The first two logs are network connections related to PowerShell network activities. However, Event ID 13 contains the changes done to the Windows Registry Key.
Here, you can see the image process that created this log. In this case, powershell.exe is what started the registry key change. Under the Details field, you can see the Base64 encoded Empire stager-script. This shows how powerful a tool Sysmon can be in detecting malicious activity in a Windows environment.
Conclusion
Sysmon is a great tool to add to your security stack. It provides greater visibility than what the Windows Event Logs give you. It may not completely replace EDR, but for those who don’t have the budget, this is definitely a powerful tool to try out.
I hope this article gave you a little more insight into Sysmon and what it can do. Please stay tuned for more content, and thanks for reading!
Resources:
- Jymcheong’s SysmonResources – https://github.com/jymcheong/SysmonResources
- TrustedSec’s SysmonCommunityGuide – https://github.com/trustedsec/SysmonCommunityGuide
- SwiftonSecurity’s Symon Config – https://github.com/SwiftOnSecurity/sysmon-config
- Implementing Sysmon and AppLocker by Black Hills Security (Webcast) – https://www.youtube.com/watch?v=9qsP5h033Qk
As a Managed Service Provider (MSP) and Managed Security Services Provider (MSSP), we manage your IT services, offer backup and disaster recovery, and provide network visibility and security. Our knowledgeable and customer-oriented staff engages to accelerate your network and simplify its security, visibility, and automation.
Questions? Contact Tec-Refresh, Inc.
