With poor security practices being all but commonplace in our world, it is only natural that we associate errors with being strictly human errors. Sometimes organizations do a terrible job of securing customer data, and now and then, we hear of someone’s account being hacked. Contrary to what you might expect, there is a form of cyberattack out there that does not rely on exploiting poorly written code, and it also does not even take advantage of human error. What if I were to tell you that this form of attack depends on the occurrence of cosmic rays. Known as bitsquatting, this attack is genuine, and it capitalizes on how bits are stored and processed on computer hardware.
The Bit
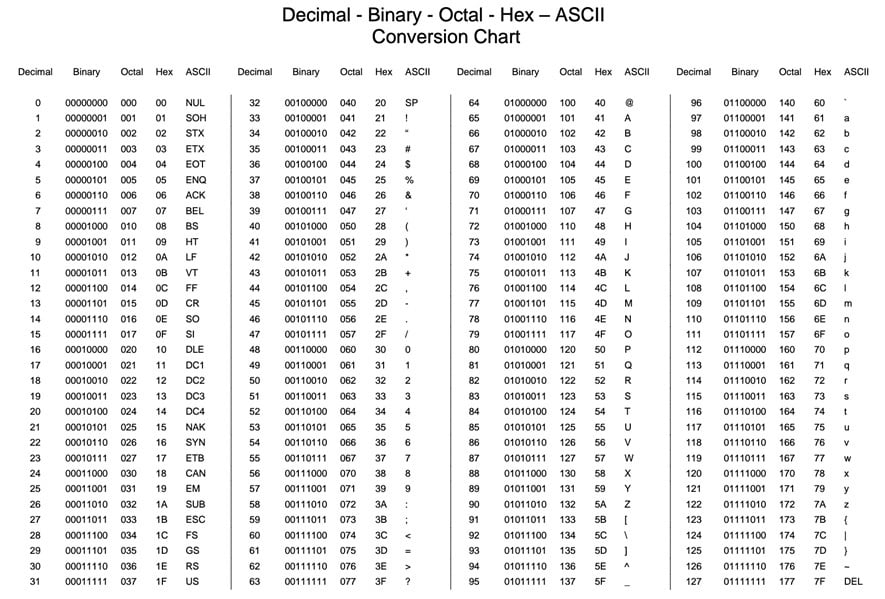
A bit is like Democritus’ conception of the atom as it is the smallest form of computer data. Bits are binary; they represent the electrical properties of either on (1) or off (0). With a large enough quantity of bits, computers can store or read a combination of bits representing a letter, a sentence, or a picture. The next unit of data, referred to as a byte, is made up of eight bits. Using the ASCII standard (American Standard Code for Information Interchange), computers can use the last seven bits in the eight bits of a byte to fully express the most commonly used characters in the English language. The mathematic equation to determine how many unique binary combinations we can have in the space of seven digits with only two options (1s and 0s) would be 27 or 128 unique combinations. For example, referring to the ASCII table, this byte: 01001101 would be represented by the uppercase letter M and the word “Hi” could be represented by two bytes: 01001000 01101001.
Errors in Computing
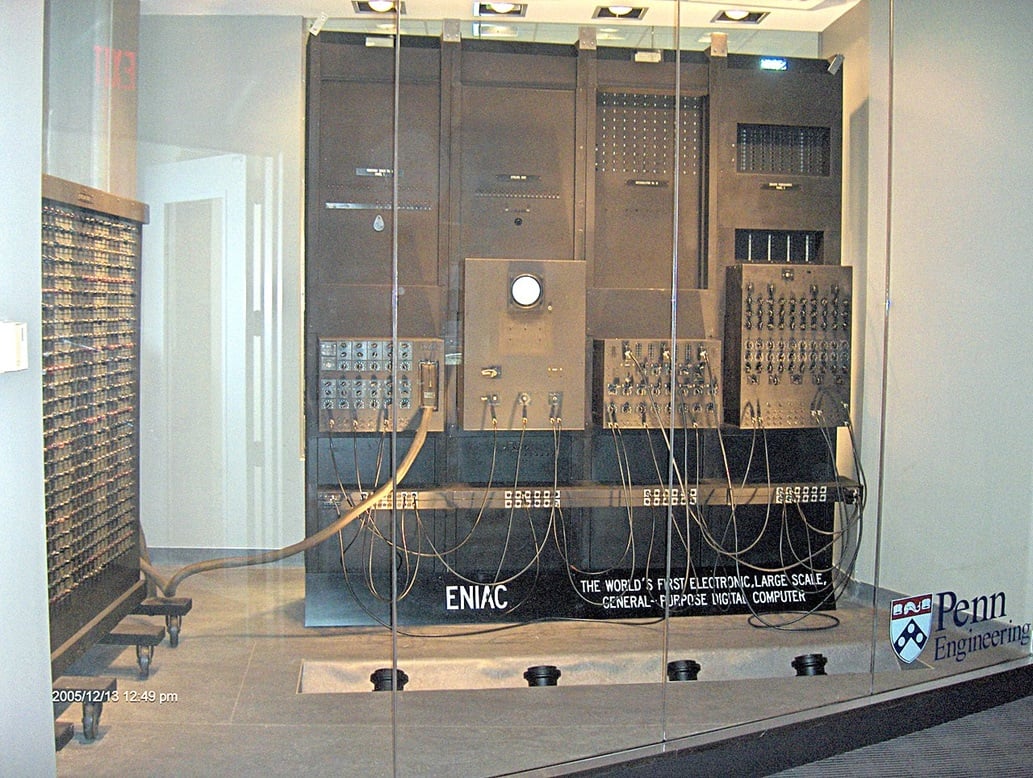
Now, what if a computer stored or misread a bit? With our previous example, if we were to switch a single bit from a 0 to a 1, or vice versa, our byte would represent a completely different character on the ASCII chart. Which highlights the issue: what if bits get changed incorrectly? This concept is not a new one and predates personal computers by almost seventy years. The ENIAC was part of the first generation of electronic computers made to solve mathematical equations. It required eighteen thousand vacuum tubes to store and process information. This antiquated form of technology was faulty, and these tubes would fail regularly. Even if the user did everything to ensure the data was input correctly, it was not uncommon for the machine to produce an incorrect answer. All the necessary tubes had to be functional for the data to be read and processed correctly.
Modern computing, which is now considered the third generation of computers, has shifted away from the vacuum tube form of information processing. Computers are now much smaller and use significantly less energy than before, but the issue of faulty hardware has continued to be a relevant topic. In his landmark presentation on bitsquatting at DEF CON 19, Artem Dinaburg demonstrated that modern computers are liable to have bit errors in memory where the electrical representation of a 1 could be changed to a 0 and vice versa.1 This can happen in multiple ways: heat, electricity, bad hardware, and yes, cosmic rays all have the capacity to cause errors. Highlighting the need for computers to operate in an ideal environment, excessive heat can affect how electricity flows and how electricity is resisted on computer hardware. Electricity can be another issue if the input voltage is erratic; it has the potential of malfunctioning electronics. Non-reliable hardware can be another issue where poorly made capacitors on a motherboard improperly store electrical charges. Dinaberg also gives the example of Intel’s 2107 DRAM chip, which was made with components that had become radioactive from a uranium mine nearby. These chips would release alpha particles, which could change or flip a bit in memory through the energy emitted. This would make it such that any software, no matter how well written, was liable to crash.
When it comes to energy-related bit errors, cosmic rays are not very different. In a follow-up to Dinaberg’s speech on bitsquatting, during DEF CON 21, Jaeson Schultz suggested that cosmic rays can impact the earth at ten thousand square meters per second.2 This means the earth is being hit with intergalactic energy rays impacting the earth at the size of two football fields every second. Referencing an IBM journal entry, Dinaberg mentioned that cities with a higher altitude have less protection against cosmic rays; therefore, computers in Denver, Colorado would be more susceptible to bit errors in memory than cities at sea level.
Dinaberg’s Bitsquatting Experiment
Dinaberg realized this type of random error can be predicted to some degree. Bitsquatting, like typosquatting attacks, anticipates errors. As explored through our previous post, typosquatting attacks take advantage of human input errors when accessing a domain. Bitsquatting, on the other hand, relies on computer errors to direct users to unintended websites. Dinaberg considered the idea that a single bit error for a domain name in RAM could lead someone to the wrong website. With the example of microsoft.com, Dinaberg registered domain names that were only different by a bit. To revisit ASCII, if the letter “r” had its second bit changed then it would become the number “2.” Dinaberg registered domain names such as mic2osoft.com, eicrosoft.com, and iicrosoft.com, amongst many others. He noticed that he was, in fact, getting HTTP requests for the website mic2soft.com. In one day, he received one thousand six hundred unique HTTP requests and visits. If an error occurred on the host computer’s memory, then that computer would request the IP address for mic2soft.com and attempt to access it. Dinaberg also registered a domain name one bit away from the website that Facebook points to as an ad server. He suggested that a bit error must have changed the ad server URL on Facebook’s server, and instead of pointing to fbcdn.net, Facebook would now be pointing to fbbdn.net. This meant that until the URL expired from the cache, clients would be redirected to a completely different website. Dinaberg also noticed bit errors occurring with internet service providers (ISP) when resolving DNS names. He registered the domain s0.2-dn.net which was one bit away from the ad server s0.2mdn.net. When the ISP would request the IP address for the bitsquatted domain, Dinaberg would respond with his IP address for the intended and bitsquatted domain. Since the DNS cache was empty for both websites, he was able to poison the ISP’s DNS server and point traffic heading to s0.2mdn.net his way.
More Work Needs to be Done
Bitsquatting attacks highlight the reality that human beings and computers are both liable to error. One way for an organization to prevent bitsquatting attacks in the past was to purchase as many bitsquattable domains as they could. A more viable option would be to replace hardware in computers and servers with error correction code (ECC) memory hard drives, RAM, and network cards. As the name suggests, ECC memory has the capacity to correct itself if it can detect bit errors. Schultz notes that there are also creative ideas that can be used to mitigate bitsquatting attacks. DNS servers can anticipate and drop domain requests they believe have bit errors. Companies can also try to reduce or eliminate the number of times full web addresses are referenced in HTML. It is worth noting that it has almost been a decade since the publishing of this article that Dinaberg decided to conduct his bitsquatting experiment and seven years since Schultz did his own. It goes without saying that the threat landscape has certainly adapted by virtue of time and awareness on the issue, but the question is, how does it look now. Is bitsquatting still a viable modern threat? It looks like we will have a better idea once the next Dinaberg or Schultz is ready to explore the issue again.
Sources
- https://www.youtube.com/watch?v=9WcHsT97suU&ab_channel=DEFCONConference
- https://www.youtube.com/watch?v=j2FVFVHVvgg&feature=share&ab_channel=RSAConference
- https://www.osti.gov/etdeweb/servlets/purl/20435900
- http://web.cecs.pdx.edu/~cgshirl/Documents/2005%20Baumann%20Soft%20Error.pdf
- http://dinaburg.org/bitsquatting.html
As a Managed Service Provider (MSP) and Managed Security Services Provider (MSSP), we manage your IT services, offer backup and disaster recovery, and provide network visibility and security. Our knowledgeable and customer-oriented staff engages to accelerate your network and simplify its security, visibility and automation. Questions? Contact Tec-Refresh, Inc.
